Security best practices
To protect your cryptocurrency, use cold wallets for secure storage, enable two-factor authentication (2FA), update software regularly, and back up private keys. Avoid common scams like phishing and fake investment schemes. Following these steps helps safeguard your digital assets from threats.
Written by Kacper Tomasiak
Sep 24, 2024
Coins are like gold nuggets in the wild west of cryptocurrencies. Freedom, decentralisation, and the possibility of significant profits make it irresistible. However, there are dangers, just like in every treasure hunt. Your crypto experience can rapidly become a nightmare due to hackers, scammers, and basic errors.
The best security advice for safeguarding your digital assets will be covered in this guide. These useful pointers can help you stay safer when navigating the crypto world, regardless of your level of experience or desire to improve your security knowledge.
Keep your keys safe
Store your private keys in a secure, offline location. Writing them down and keeping them in a safe is far more secure than saving them digitally on a computer or cloud service. For even better protection, consider using a hardware wallet. These physical devices keep your private keys offline, shielding them from online threats.
The mantra in the crypto world is simple: “Not your keys, not your coins.” If you rely on an exchange or other third party to hold your keys, you relinquish control of your funds. Owning your private keys ensures true ownership.
Strong passwords and two-factor authentication
Use strong passwords
A strong password is your first line of defense against unauthorized access. Simple passwords, like “123456” or your pet’s name, are easy for hackers to guess. Instead, opt for complex passwords that combine upper- and lowercase letters, numbers, and special characters.
Enable 2FA
Equally important is enabling two-factor authentication (2FA) on all your crypto-related accounts. 2FA requires a second form of verification, such as a code from an authentication app, before granting access. This adds an extra layer of security, making it much harder for attackers to gain entry.
Avoid relying on SMS-based 2FA, as phone numbers can be hijacked through SIM-swapping attacks. Apps like Google Authenticator or Authy provide a safer alternative.
Secure your devices
Your smartphone, tablet, or computer is a vital part of your crypto ecosystem. Securing these devices is non-negotiable. Install reputable antivirus software to defend against malware and keyloggers, which can record your keystrokes and steal sensitive information.
Regularly update your device’s operating system and apps to patch vulnerabilities. Cybercriminals often exploit outdated software to gain access. Avoid accessing crypto wallets or exchanges on public Wi-Fi networks, which are easy targets for hackers. If you must use public Wi-Fi, protect yourself with a Virtual Private Network (VPN).
Encrypting your devices adds an extra layer of security. This ensures that even if your device is stolen, accessing your data becomes significantly more difficult for the thief.
Recognize patterns and avoid scammers
Identify phishing attempts
The crypto space, while revolutionary, is also rife with scams targeting unsuspecting users. Phishing scams are among the most prevalent. Scammers send fake emails or messages pretending to be from exchanges, urging you to click on malicious links or share your credentials. Always verify the source of communication and access exchanges directly via bookmarked URLs.
Ponzi schemes often promise life-changing profits and encourage you to refer friends.
Don’t fall for ponzi schemes
Fake investment schemes often promise unrealistically high returns, urging you to “invest now before it’s too late.” These are classic red flags. Cryptocurrency is volatile, but legitimate investments don’t come with guarantees of doubling your money overnight. Conduct thorough research before investing in any platform or project, and avoid offers that sound too good to be true.
Use cryptocurrency exchanges wisely
Exchanges are gateways to buying, selling, and trading cryptocurrencies. However, they are also prime targets for cyberattacks. High-profile hacks, such as the Mt. Gox breach, highlight the risks of keeping funds on exchanges.
To minimize exposure, avoid storing significant amounts of cryptocurrency on exchanges for extended periods. After making a purchase or trade, transfer your funds to a secure wallet. Choose reputable exchanges that have a track record of strong security measures, and activate all available security features, such as 2FA and withdrawal whitelisting.
While exchanges are necessary for trading, treat them as temporary holding places rather than permanent storage solutions.
Choose the right wallet
Wallets are essential tools for storing and managing cryptocurrency. Choosing the right one depends on your requirements.
Hot wallets, connected to the internet, are convenient for frequent transactions but are more susceptible to hacks. Popular examples include MetaMask and Trust Wallet. On the other hand, cold wallets, which are offline, offer superior security and are ideal for long-term storage. Hardware wallets like Ledger and Trezor are excellent choices for serious investors.
For enhanced security, diversify your storage. Use hot wallets for day-to-day transactions and cold wallets for the bulk of your holdings. This ensures that even if your hot wallet is compromised, your main funds remain safe.
Practice safe transactions
Always double-check
When sending cryptocurrency, always double-check wallet addresses. Crypto transactions are irreversible, and even a single incorrect character can send funds to the wrong address. To minimize errors, copy and paste addresses and verify them thoroughly before hitting send.
Send test transactions
For large transactions, practice caution by sending a small test amount first. Once the test transaction is successful, proceed with the full transfer. This step adds an extra layer of assurance, especially when transacting with new or unfamiliar wallets.
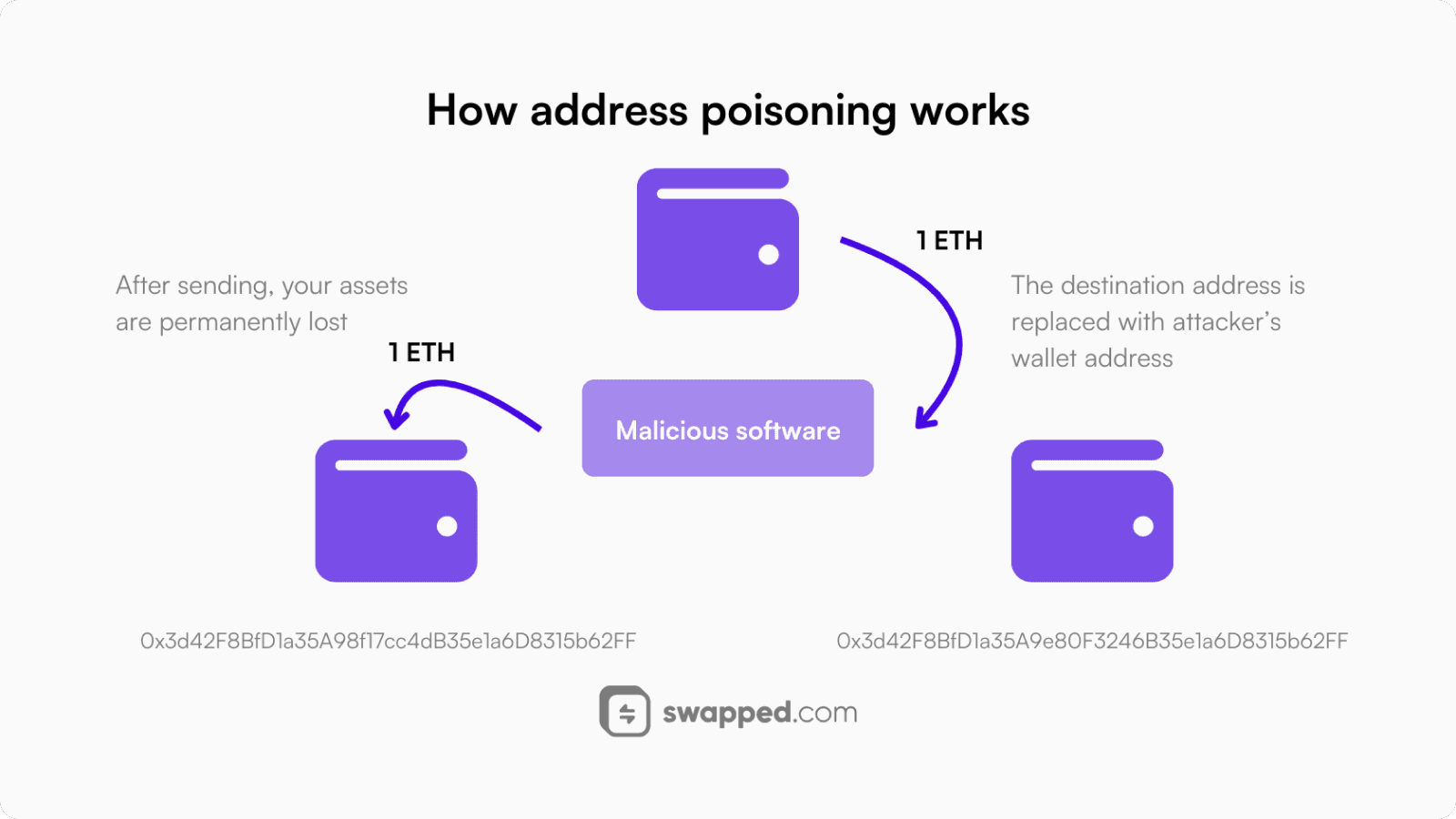
Remember to carefully check the destination address as blockchain transactions are irreversible!
Not your keys, not your coins
Custodial wallets, often provided by exchanges, manage your private keys for you. While convenient, this setup places your funds at risk if the exchange is hacked or fails.
Non-custodial wallets, where you control the private keys, offer true ownership and peace of mind. Although they require more responsibility, they ensure that your funds remain under your control. As the crypto community often says, “If you don’t control the keys, you don’t own the coins.”
The responsibility is yours
Imagine stepping into the world of cryptocurrency, full of excitement and potential, only to make a simple mistake that costs you everything. For many, such a moment can define their journey—but it doesn’t have to.
By following these security best practices, you’re not just protecting your digital assets; you’re taking control of your financial future. Each step you take, from securing your private keys to avoiding scams, makes you a more experienced cryptocurrency enthusiast.
Let your story be one of smart choices and foresight. The tools are in your hands—use them wisely to protect your assets and ensure their growth for years to come.
Resources
If you're interested in diving deeper and expanding your knowledge of best security practices, here are some suggestions: